If we look at the history of payment transactions, beginning first before any electronic conveniences one should take the money first to the bank by lining up at the counter so they should take the money to use for a certain period of time considering a sizable effort to take some money. With the automated teller machines (ATMs), everywhere attempt to take the money be light enough so a person taking money for short periods. In addition, holders of ATM reduces the risk of money from the crime of theft / robbery / etc because the money taken is usually less when compared with taking money at the bank counter.
With the development of information and communication
technology (ICT), new electronic payment instruments that became popular in Indonesia, such as credit cards and debit cards. Both types of payment using smart card payment terminals are rubbed into the stores when paying. Smart card to replace the physical money that is usually stored on a smart card wallet so that users can avoid the crime and also get the convenience of users, ie do not need to take the money into a bank or ATM and store in a wallet.
Of course, smart card payment system must have a
security system that ensures money is not taken by the user who is not entitled to and also there was no immediate claim payments that never made the user. Without the guarantee of security systems in smart card payment system, users will not be interested to use it.
At present, in addition to obligatory wallet mobile phone bring in travel. It gives ideas for innovators to combine wallet and mobile phone. There have been innovative from a mobile service provider to make payments using SMS and mobile web. A consortium of producers in the world
mobile phone giants finally work together to create new products to combine with a mobile wallet with a Near Field Communications (NFC).
Actually, the NFC is the development of card technology Radio Frequency Identification (RFID). RFID has the same form and function like an ATM card is different from RFID cards do not need to be polished (contactless) thus RFID cards do not need to be removed from the wallet in the payment process, users simply hold the purse to the payment terminal or reader called. In Indonesia, RFID cards are widely used, for example: e-Toll for automatic payment of toll gates, bracelets (RFID tags, not the shape of the card) is used instead of tickets at amusement parks.
NFC technology on
mobile phones a step further than where RFID
technology in mobile embedded NFC chip that can act as an RFID card and also as a reader at once with a short range radius (less than 10 cm). NFC
technology on mobile phones can truly replace the wallet in which to spend money and also received money from and to fellow users NFC. In addition to payment of NFC
technology can be used as a replacement ID card, driver's license, student card, etc., time card, and others.
It is planned that by 2011 it would appear many leading mobile products equipped with NFC technology. The first mobile product with NFC technology is already marketed in Europe and America is the
Samsung Nexus S, completed NFC controller chip products NXP (Philips), namely PN544. Philips is a leading manufacturer of RFID cards. Samsung Nexus S uses the Android operating system version supported by Google's Gingerbread. Google itself has prepared a variety of applications for NFC technology on
mobile phones.
Many jokes about printing machine that works hard 24 hours a day to produce the amount of money very much for a very large fund expenditures. But on the other hand, the use of physical cash is on the decline worldwide, due to non-cash payments are growing in popularity. Although, according to economists in the money increases, the amount of paper money people are putting in the wallet tends to decline. This can be seen from the increasing number of credit and debit card transactions worldwide. Analysts predict that the top three regions in mobile payments is the Far East including China, Western Europe and the United States, which as a whole will account for more than 70 percent market share in mobile payment gross transaction basis by 2013.
School of Electrical Engineering & Informatics, Bandung Institute of Technology, is active-very jealous conduct research to develop Transaction System Using
Mobile Phone and NFC Technology with a grant from the Incentive Program, Ministry of Research and Technology. NFC Research Group had been formed. The purpose of this research is to produce a transaction system with NFC technology on
mobile phones for micro payment (payment with a small amount, for example: public transportation, shop, canteen, etc.) and macropayment (payments with a larger number, for example: supermarket, mini market, restaurant , various shops, etc.).
This transaction system to be very safe for users, sellers, and users of the financial industry so that money can not be reduced / increased improperly; seller get the money that should be, and the financial industry does not lose money and not have to pay should not. Let's welcome the presence of NFC technology for shared prosperity.
 With more and more and the development of the Linux Operating System, especially the many free Linux distributions that we can use such as Ubuntu, Kubuntu, Fedora, PCLinuxOS and others, might make some who have never tried curious. For Windows users, there are alternatives to try without having to install on your computer, using a USB stick only.
With more and more and the development of the Linux Operating System, especially the many free Linux distributions that we can use such as Ubuntu, Kubuntu, Fedora, PCLinuxOS and others, might make some who have never tried curious. For Windows users, there are alternatives to try without having to install on your computer, using a USB stick only.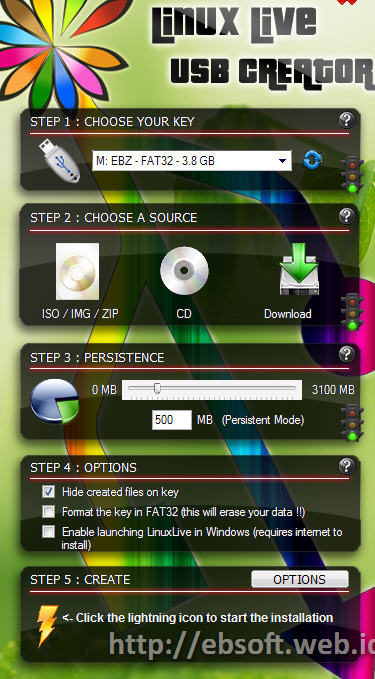







 If we look at the history of payment transactions, beginning first before any electronic conveniences one should take the money first to the bank by lining up at the counter so they should take the money to use for a certain period of time considering a sizable effort to take some money. With the automated teller machines (ATMs), everywhere attempt to take the money be light enough so a person taking money for short periods. In addition, holders of ATM reduces the risk of money from the crime of theft / robbery / etc because the money taken is usually less when compared with taking money at the bank counter.
If we look at the history of payment transactions, beginning first before any electronic conveniences one should take the money first to the bank by lining up at the counter so they should take the money to use for a certain period of time considering a sizable effort to take some money. With the automated teller machines (ATMs), everywhere attempt to take the money be light enough so a person taking money for short periods. In addition, holders of ATM reduces the risk of money from the crime of theft / robbery / etc because the money taken is usually less when compared with taking money at the bank counter.